
As connectivity increases, new openings emerge for cyberattacks. Consequently, UNECE regulations require that OEMs and fleet operators provide effective security risk management for vehicles throughout their life cycle. One of the key elements for achieving this is attack detection via intrusion detection systems (IDS) in the vehicle. But how can reliable monitoring of on-board network communication via IDS still be guaranteed in the future, even under the increased requirements of Ethernet-based E/E architectures?
ETAS is offering a solution that is tailor-made for current and future vehicles with its ESCRYPT IDS sensors CycurIDS-CAN for CAN/CAN-FD networks, CycurIDS-ETH for Ethernet networks, and host-based IDS tailored to automotive ECUs. The IDS manager ESCRYPT CycurIDS-M and the IDS reporter ESCRYPT CycurIDS-R complete the offer.
An immune system for vehicles
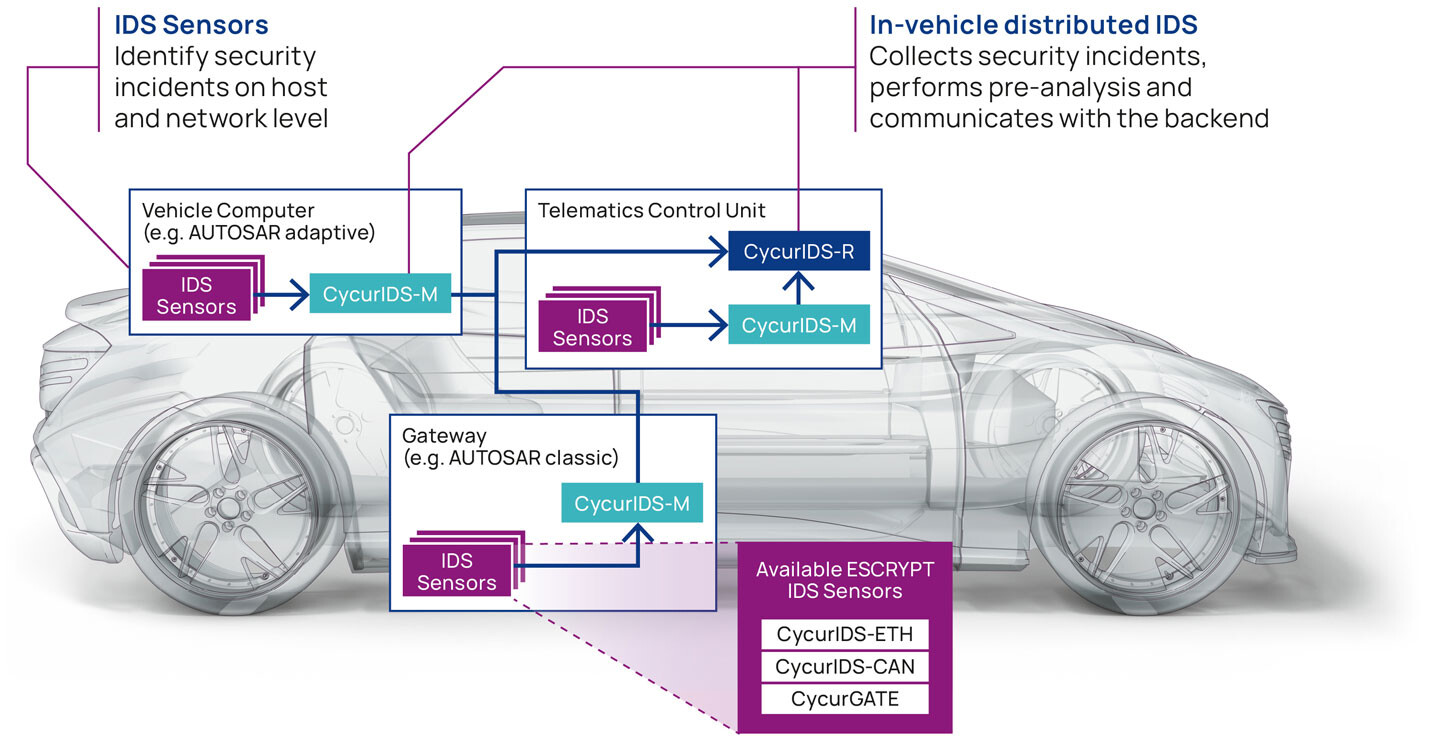
The main task of an IDS is to identify attacks on the vehicle and report them to a vehicle security operations center (VSOC), from where appropriate countermeasures can be initiated. To fulfill this task, a distributed IDS in the vehicle comprises several components: IDS sensors (ESCRYPT CycurIDS-CAN & ESCRYPT CycurIDS-ETH), IDS manager (ESCRYPT CycurIDS-M), and an IDS reporter (ESCRYPT CycurIDS-R). The in-vehicle components and the V-SOC forms the IDPS solution, which enables manufacturers and fleet operators to establish a life cycle of continuous security improvements.
Security guard for electrical system communications
- Timely detection of attacks in the field
- Field-proven ready-to-use solution
- Holistic offering that covers IDS sensors, security event management and reporting for in-vehicle intrusion detection
- In-vehicle IDS components are part of the ESCRYPT Intrusion Detection and Prevention Solution
(IDPS), that includes also a VSOC as a managed security service - Components are compliant to AUTOSAR, fulfill current automotive quality requirements, and are optimized for resource constrained ECUs
- A white-box, transparent security approach that enables you to realize and control your own cybersecurity policy
- Compliance to upcoming legal requirements, e.g. UN R155
Further details
- Monitoring of forwarded CAN traffic & detection of potential attacks (anomalies)
- Configuration GUI provided automatic rule generation and simulation
- Reporting and logging of anomalies, either locally or to Vehicle SOC
- Heuristic and signature-based detection on ECU
- ESCRYPT CycurIDS-CAN is fully interoperable with the IDS manager concept and can be incorporated as a “smart sensor” to detect intrusions on CAN
The calibration of ESCRYPT CycurIDS-CAN is based on manufacturer-specific configuration data (DBC/ARXML) for vehicle CAN networks. This configuration is optimized and validated by running a simulation based on recorded network traffic. The result is a high detection rate coupled with a low number of false alarms.
- Enables you to observe message frequency to detect “message injection”
- Allows to compare all messages on the busses with a whitelist to detect unspecified messages
- Detects malicious diagnostic requests while driving, e.g. detect attempts to shutdown certain ECU
- Security event management for automotive ECUs
- Comes in two product variants:
-
for deeply embedded ECUs, i.e., μCs with classic AUTOSAR or RTOS
-
for larger platforms i.e., μPs running adaptive AUTOSAR and/or some POSIX OS
-
- AUTOSAR compliant solution that is designed to be flexibly extended to cover any customer aggregation, persistence or reporting strategy
- Allows selection of relevant security events as early as possible to reduce storage and bandwidth cost
- Easy vehicle wide configuration that can be adapted according to generated security events
- Monitoring of Ethernet traffic & detection of potential attacks (anomalies)
- Configuration GUI provided automatic rule generation and simulation
- Reporting and logging of anomalies, either locally or to Vehicle SOC
- Heuristic and signature-based detection on ECU
- Ready-to-use software solution to enable in-vehicle intrusion detection for current and future Ethernet based E/E architectures
- ESCRYPT CycurIDS-ETH can run entirely on Ethernet switch as well as uC/uP
The configuration of ESCRYPT CycurIDS-ETH is based on manufacturer network description files e.g. ARXML for vehicle ethernet network. This configuration is optimized and fined tuned futher using the configuration tool GUI.
- Offers specification based intrusion detection
- Allows anomaly based intrusion detection
- Detects malicious diagnostic requests while driving, e.g. detect attempts to shutdown certain ECU
- Security event reporting for the vehicle
- Customized solution connecting the vehicle to the Vehicle Security Operations Center (VSOC)
- Encapsulated provision of the IDS communication functionality
- Allows isolated deployments to fulfill security requirements
- Seamless integration with ESCRYPT CycurIDS components
Cooperation of ETAS and NXP Semiconductors

ETAS offers ESCRYPT CycurIDS-CAN tailored to NXP's secure CAN transceiver to utilize hardware support for IDPS systems. Benefits are among others the precise rogue sender identification and the prevention of network impact. Watch this video to get more information our reach out to us for a live product demo!

Security strategy for the entire vehicle life cycle
Intrusion detection and protection calls for continuously effective, comprehensive security mechanisms. To this end, the ESCRYPT CycurGATE embedded firewall protects vehicle ECUs and networks against all known attack patterns. In addition, ETAS offers a cyber defense center backend: ESCRYPT CycurGUARD. This evaluates notifications from IDS components, detects new attack trends, helps determine the causes of security incidents, and defines countermeasures for distribution throughout the vehicle fleet.
