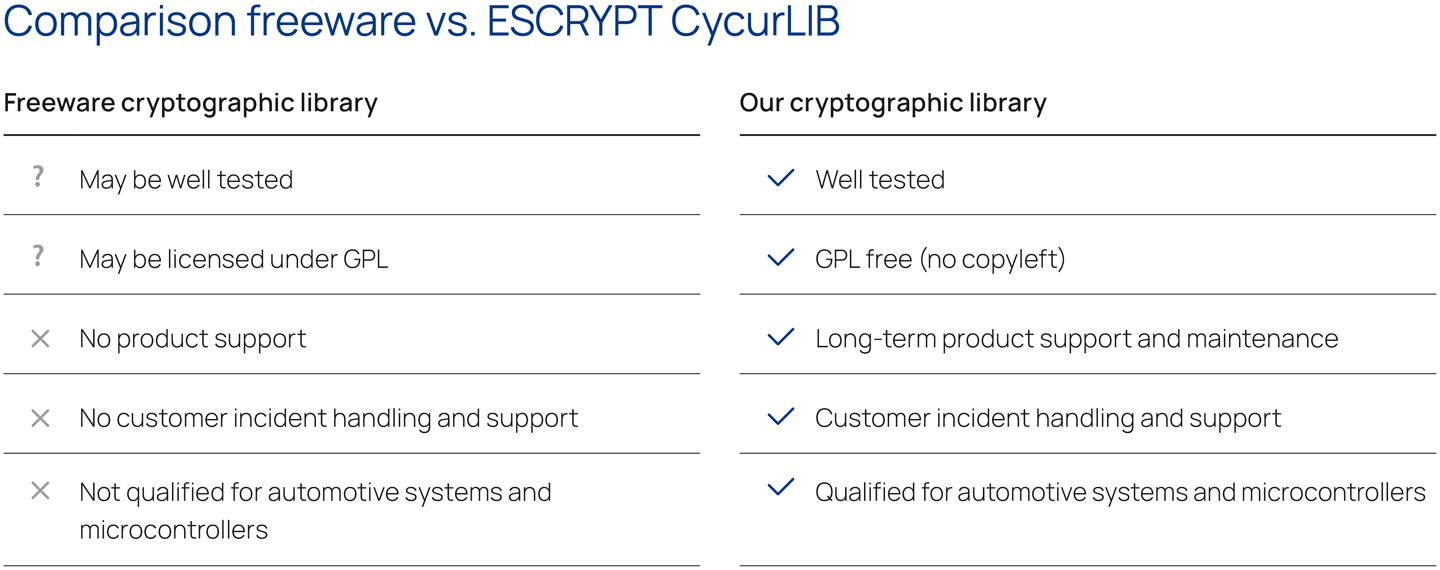
Cryptographic operations and algorithms provide the fundamental basis for virtually all IT security applications. For example, cryptographic algorithms such as digital signature verification are required for flash solutions, feature activation, and secure boot.
ETAS offers the perfect cryptographic library to meet these needs in the form of ESCRYPT CycurLIB. Specially geared to the requirements of embedded systems, ESCRYPT CycurLIB has acquired a solid reputation over many years for its outstanding performance in resource-constrained environments.
Making security simple
ESCRYPT CycurLIB offers a simple way to make your products more secure, for example by verifying digital signatures to determine the authenticity of a data source or by encrypting data to ensure confidentiality. ETAS’ cryptographic library for embedded systems is also highly configurable and can be tailored to your specific needs.
The right code for your applications
- Sound
Is developed with ASPICE (level 2) and ISO 26262 (up to ASIL D) compliant processes - Comprehensive
Supports all common cryptographic algorithms and certificate standards (incl. Chinese Standards) - AUTOSAR compliant
Supports AUTOSAR and non-AUTOSAR configuration. - Flexible
Runs on all platforms and can be optimized for different processors with regard to speed, RAM, and ROM - Customizable
Is designed to be modular, so you only use the algorithms you actually need - Low footprint
Has an impressively small resource footprint and low resource consumption
ESCRYPT CycurLIB Cryptographic Library
| Category | Algorithms |
|---|---|
|
Hash Functions |
SHA-2 |
|
Symmetric Encryption |
AES, ChaCha20 |
|
Message Authentication Codes (MAC) |
HMAC with SHA-2, CMAC with AES, SipHash |
|
Random Number Generation |
Hash-DRBG, HMAC_DRBG |
| Category | Algorithms |
|---|---|
|
Signature Generation and Verification |
RSA with PKCS#1-PSS / PKCS#1-V1_5, ECDSA, Ed25519 |
|
Key Generation |
Curve25519 |
|
Key Agreement |
Curve25519, ECDH |
|
Certificates |
X.509 parser |

