Cybersecurity included
Security for AUTOSAR Adaptive architectures

AUTOSAR Adaptive paves the way to an intelligently connected vehicle. To provide reliable protection against cyberattacks, this standard features security functions that can be integrated today into tomorrow’s E/E architectures.
E/E architectures with signal-based connectivity and functionally partitioned ECUs are reaching their limits when it comes to connected and highly automated vehicles. Calls for autonomy and connectivity lead to centralized high-performance vehicle computers (VCs) and domain controllers (DCUs) making strategic decisions, and sensor and actuator ECUs simply executing the commands.
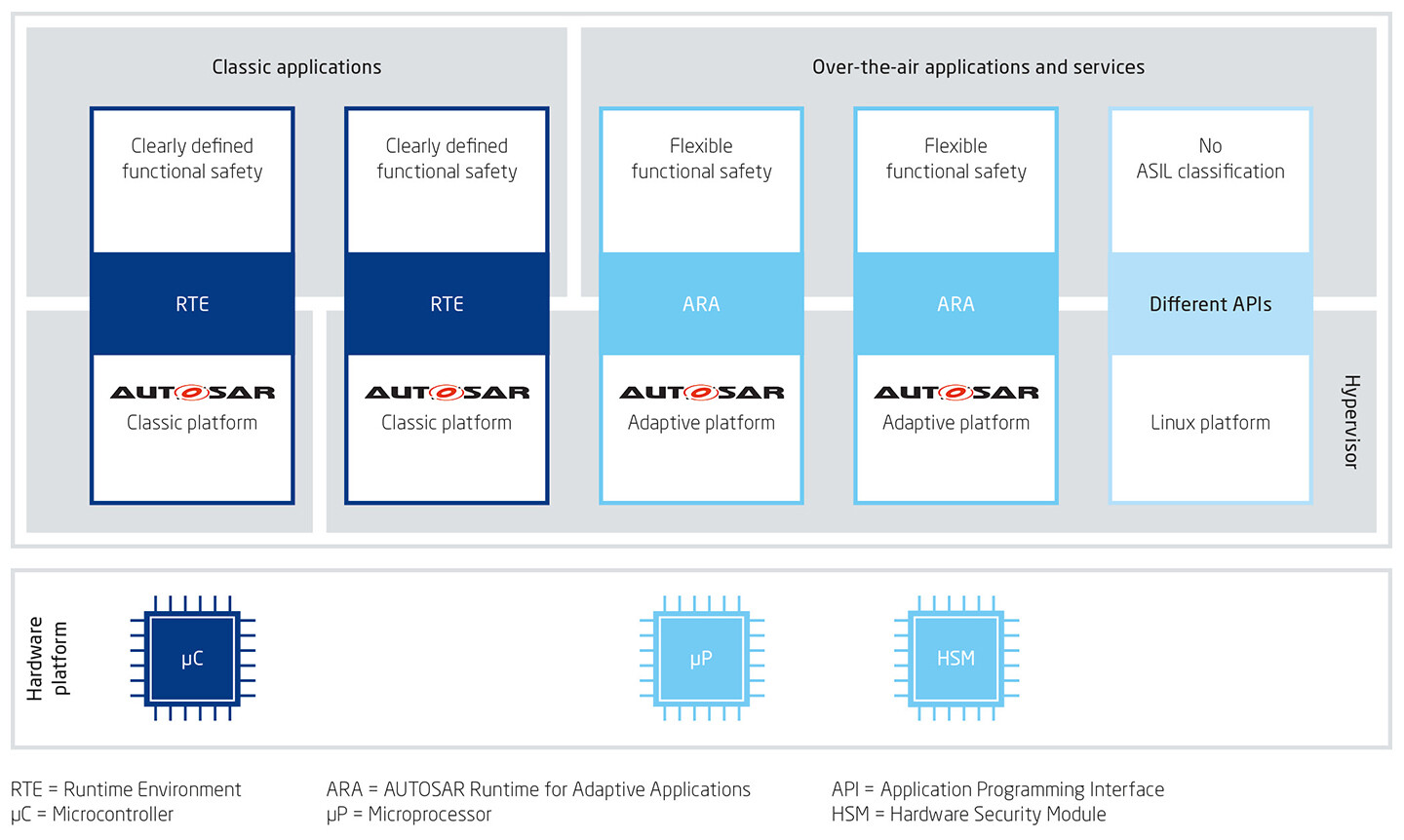
The AUTOSAR Adaptive platform provides the framework for these new E/E architectures. It makes it possible to dynamically adapt application software and uses the AUTOSAR Runtime for Adaptive Applications (ARA) interface to establish a connection with a POSIX-based operating system, such as Linux (Fig. 1). To ensure that software from different vendors and of different ASIL categories run safely on the VC, hypervisors are used to preconfigure partitioning.
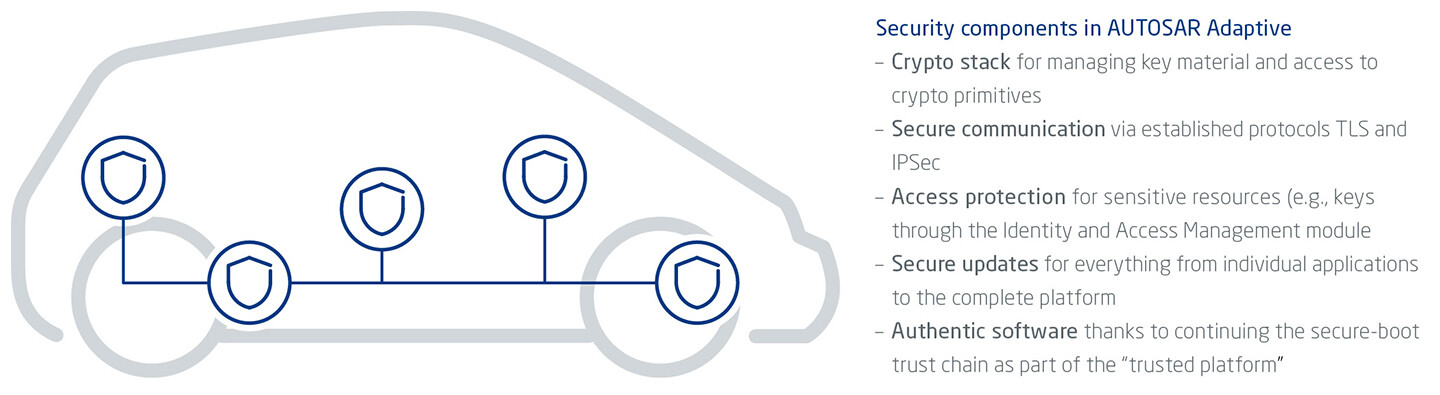
Cybersecurity management
Smart connected vehicles cannot be secured with individual measures., but only with integrated concepts based on risk analyses of the entire vehicle architecture. These concepts must be broken down to the security requirements of individual components, ECUs, and their logical partitions. Accordingly, AUTOSAR Adaptive features an integrated basic set of security functions that developers can use to address the shifting quantitative and qualitative protection requirements of connected, automated vehicle systems. Given that distributed, software-based E/E architectures drive up data loads under real-time conditions, security measures must be designed to perform better. This is why the following security functions have been integrated into AUTOSAR Adaptive (Fig. 2).
Cryptography as a “key component”
Many security use cases rely on cryptographic primitives to, for example, encrypt confidential data or verify the signature of software updates. The cryptographic keys and certificates required to do so must be stored securely, managed by an authorized application, and sometimes even synchronized across several ECUs. In AUTOSAR Adaptive, these primitives are provided through the cryptography functional cluster (also called crypto API). It offers an abstraction of the interfaces provided and thus increases overall software portability.
To ensure secure data exchange, AUTOSAR Adaptive follows the latest standards, including TCP/IP communication via Ethernet. Using TLS and IPSec – the established protocols within the world of IT – it is possible to set up secure channels for communication within the vehicle and with external instances that are impervious to manipulation or eavesdropping.
AUTOSAR Adaptive manages access to system resources such as persistent memory, communication channels, and cryptographic keys. The AUTOSAR Identity & Access Management module provides a gatekeeper that allows only explicitly authorized applications to access the respective resource. Access rights can be configured as required and updated at any time.
Secure update and trusted platform
The secure update function in AUTOSAR Adaptive helps to fix detected vulnerabilities, for instance found by IDS (Intrusion Detection System). It receives and processes security updates for individual applications or even for the entire platform. The individual Update Blobs are signed by the back end so that only updates from a trusted source are executed.
In addition to updates, ECU and VC applications must also be verified at regular intervals. This calls for either secure boot or the trusted platform function in AUTOSAR Adaptive, which, as a trust anchor, verifies all applications as well as the platform itself. By maintaining the trust chain from boot to platform to application, only trusted software is executed.
RTA-VRTE: platform software framework for AUTOSAR Adaptive
For future users of AUTOSAR Adaptive, it is crucial to become familiar with the new architecture today. The Vehicle Runtime Environment (RTA-VRTE) platform software framework is the ideal basis for integrating and implementing security functions as well as for all other AUTOSAR Adaptive-compliant processes.
RTA-VRTE contains all the important middleware elements for microprocessor-based vehicle computers. The platform software framework enables the function of virtual ECUs to be simulated on conventional desktop PCs and networked via Ethernet. RTA-VRTE creates a virtual machine consisting of four layers of basic software architecture, with the fifth layer then containing the vehicle-specific platform services (Fig. 3).
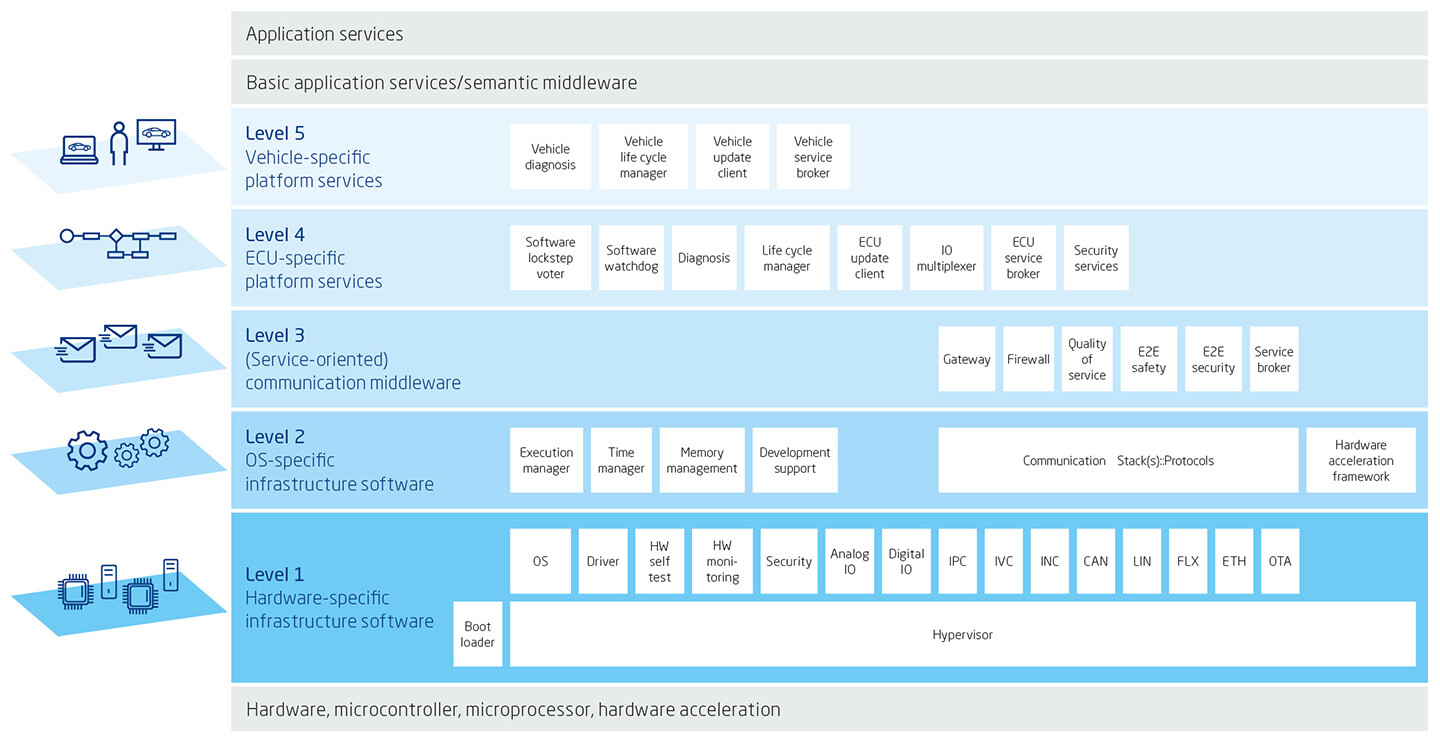
Levels 1 and 2 contain the infrastructure software for the hardware used (e.g., device drivers) and a POSIX-compliant operating system. Level 2 also provides platform-specific elements that derive from the AUTOSAR Adaptive specifications – first and foremost execution management. This manages the dynamically assigned applications, ensures that they are started and stopped correctly, and monitors adherence to the assigned resource and execution limits. Execution management is thus a key function in IT security, providing the trusted platform and verifying the integrity and authenticity of Adaptive applications. In this way, possible manipulation or damage is detected in advance.
In addition, the level 3 communication middleware ensures that the dynamic, flexible Adaptive applications and the other software applications can be integrated into the system. As a core component in RTA-VRTE, communication management controls and regulates the interaction between the levels and guarantees the smooth operation of the encapsulated software including the ECU- and vehicle-dependent platform services on levels 4 and 5. In securing end-to-end communication between services offered by authenticated applications, this function is also highly relevant to cybersecurity.
RTA-VRTE communication management together with ECU specific services on level 4 provides application developers with a versatile framework for automotive applications. To provide security, this level also features an update and configuration manager (UCM), which supports authenticated updates of individual applications and coordinates them across the entire platform. On level 5 of RTA-VRTE, the AUTOSAR++ aspect allows the integration of whole-vehicle and even fleetwide functionality, providing robust over-the-air (OTA) updates of the RTA-VRTE AUTOSAR Adaptive application set.
Outlook: comprehensive security beyond AUTOSAR Adaptive
In 2020, RTA-VRTE began to be used around the world in projects aiming to bring AUTOSAR Adaptive vehicle platforms to production. In addition, ETAS and ESCRYPT off er an Early Access Program (EAP) that enables OEMs and suppliers to establish the development methodology of next-generation hybrid E/E architectures while implementing the security components already available through AUTOSAR Adaptive.
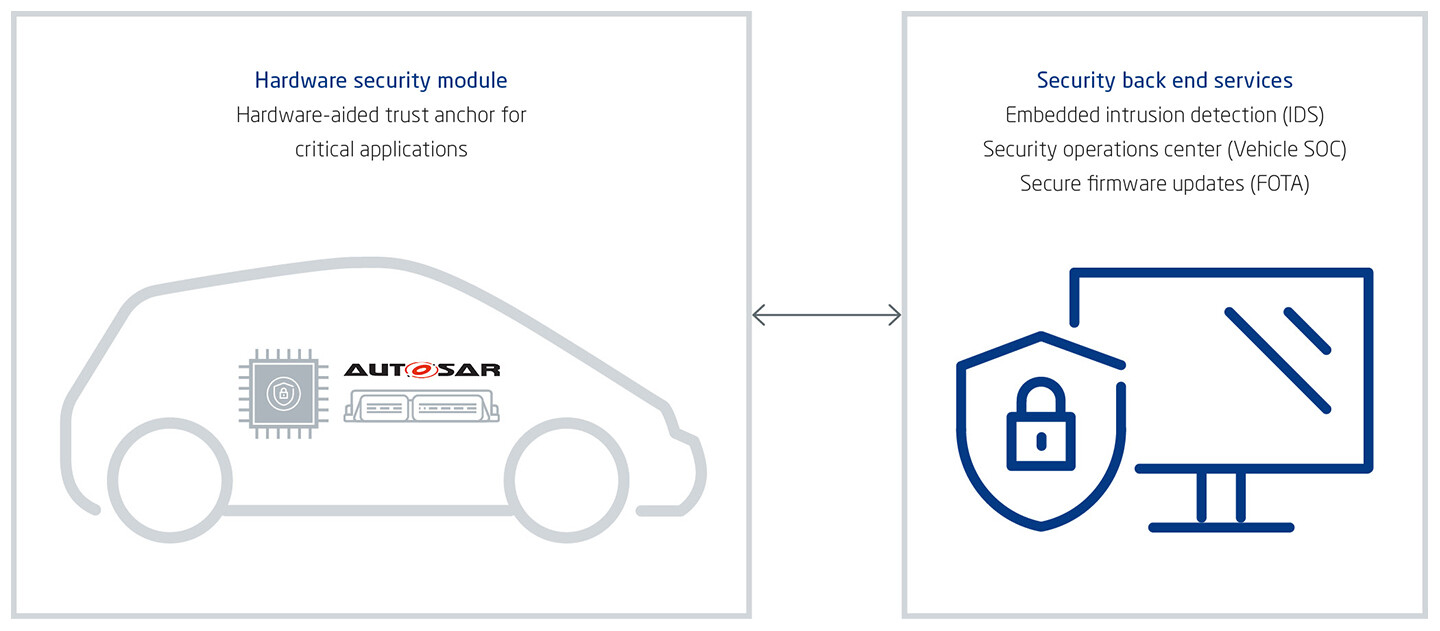
Beyond these security modules, what is required are truly comprehensive cybersecurity concepts for connected, automated vehicles. This starts with hardware security modules (HSMs) as trust anchors to physically encapsulate cryptographic key material in VC microcontrollers or in ECUs. And it extends to fleet-wide vehicle protection over the entire life cycle together with embedded in-vehicle attack detection, a vehicle security operation center (VSOC) in the back end, and firmware over-the-air (FOTA) security updates (Fig. 4).
The RTA-VRTE platform software framework enables developers to bring AUTOSAR Adaptive-based E/E architectures to life in a virtual setting today. In so doing, it expands the basis for comprehensive protection against cyberattacks, which in the vehicles of the future will have to extend from the microcontroller to the in-vehicle network and to lifelong, fleet-wide monitoring.
Authors
Dr. Michael Peter Schneider is Project Manager AUTOSAR Security at ESCRYPT GmbH.
Dr. Stuart Mitchell is RTA-VRTE Senior Product Manager at ETAS GmbH.
Further information
-
 Cybersecurity included Download
Cybersecurity included Download