Uncover the vulnerable points of your automotive systems
UN R 155 and other international regulations have made a risk-based approach to vehicle architecture development a prerequisite for type approval. In addition, ISO/SAE 21434 sets the framework for the implementation of these guidelines. Threat Analysis and Risk Assessment (TARA) has thus become an indispensable part of automotive system design and development processes.
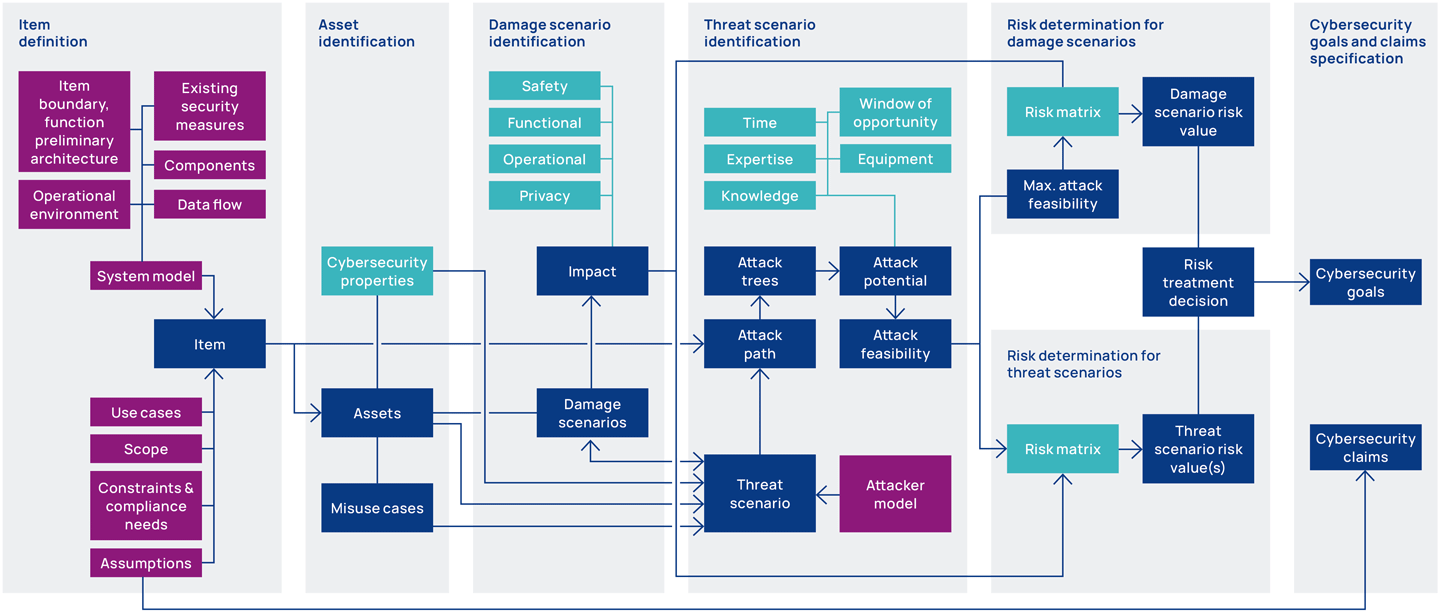
Threat Analysis & Risk Assessment methodology
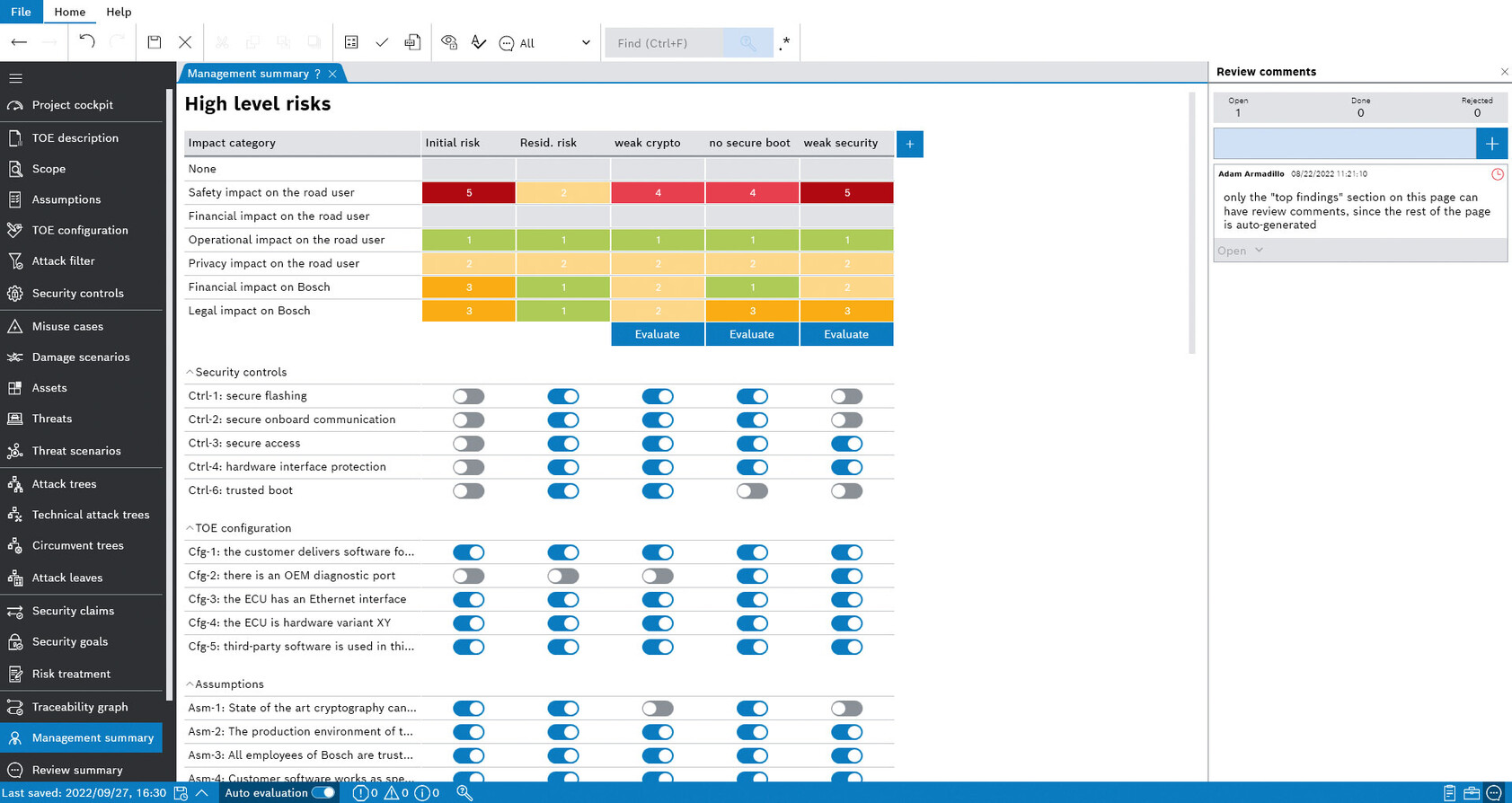
ESCRYPT CycurRISK is a TARA software tool that helps you to uncover and evaluate the potential attack surfaces in automotive systems and architectures at an early stage.
ESCRYPT CycurRISK allows you to systematically identify and analyze threats via attack feasibility (based on attack potential) using attack trees. Damage scenarios are used to assess the impact on road users and your business. The tool provides a structured documentation of threat scenarios and risks to a given system. Further, it allows to compare different variants and to share and reuse knowledge from previous analyses through catalogues. Thus, ESCRYPT CycurRISK enables you to prioritize risks and countermeasures and to create a security concept compliant to the requirements of security engineering processes, ISO/SAE 21434 and UN R 155.
Your benefits
- Established
Widely used in the automotive industry - Professional
ETAS offers professional maintenance and support - Reliable
Updates and improvements based on our long-standing experience in automotive security - Quality and reliability
Fully compliant with ISO/SAE 21434, the tool classification according to ISO 26262 is available and the tool qualification for all use cases is for tool confidence level (TCL) 2/3 performed - Flexible
The report templates are fully configurable - Comprehensive
Backed with ETAS security consulting experience and services
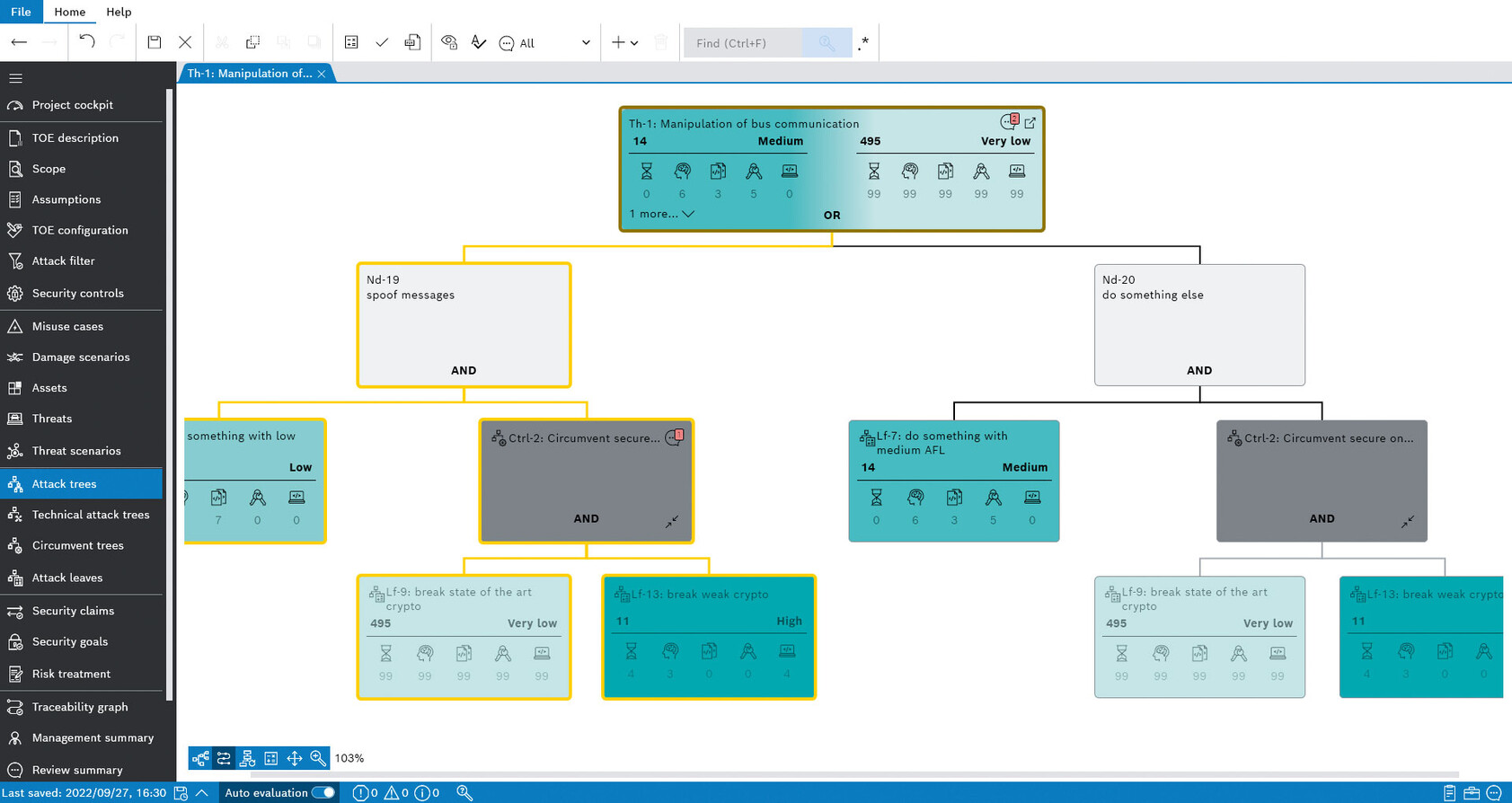
Creating TARAs efficiently
- Workflow-oriented guidance
- User-friendly GUI
- Direct comparison of initial and residual risks
- Automatic management summary
- Integrated attack tree editor
- Support of attack potential method with automatic attack potential computation
- Dedicated mode for reuse TARA
- Sophisticated functionality for variant handling and configuration
Now available: Automotive Threat Matrix

The Automotive Threat Matrix (ATM) developed by Auto-ISAC is now available as a threat library in ESCRYPT CycurRISK. The ATM is a remarkable resource that enumerates adversary tactics and supporting techniques specifically tailored to the automotive industry. The matrix is built on real-world observations, validated automotive attacks, and peer-reviewed and reproducible automotive exploit research.
With this integration into ESCRYPT CycurRISK, automotive cybersecurity professionals can leverage the ATM as a starting point for robust threat modeling. This threat library is available for free with each license of ESCRYPT CycurRISK.
To learn more about how you can access the Automotive Threat Matrix within ESCRYPT CycurRISK, reach out to our team for more information.

Professional assessment for your automotive cybersecurity during the complete product lifecycle
ETAS' threat analysis and risk assessment service supports you during the whole TARA process for embedded products in the design or development phase and in the field. Because even if product development is further along, long product lifecycles often mean having to respond to new requirements or new security risks. ETAS helps customers determine the data and functions to be protected, identify potential attacks and attackers, and define the appropriate protection requirements for all critical security risks. When necessary, ETAS develops suitable adaptations for security implications.